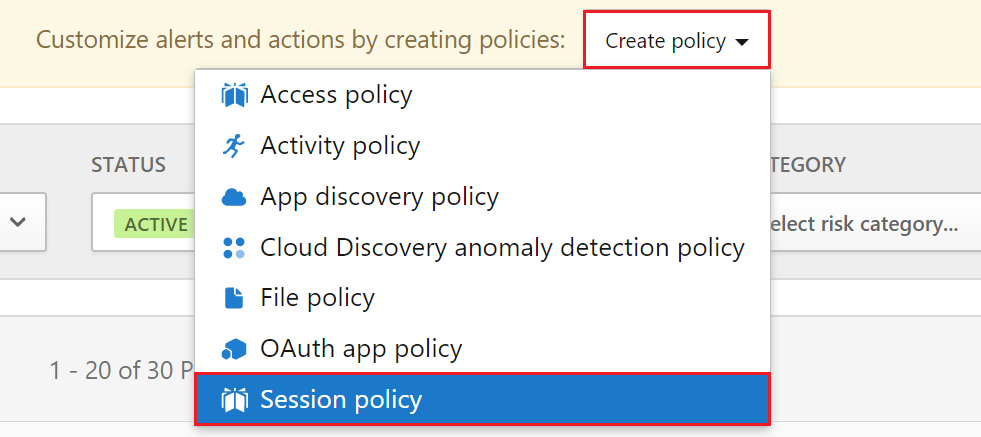
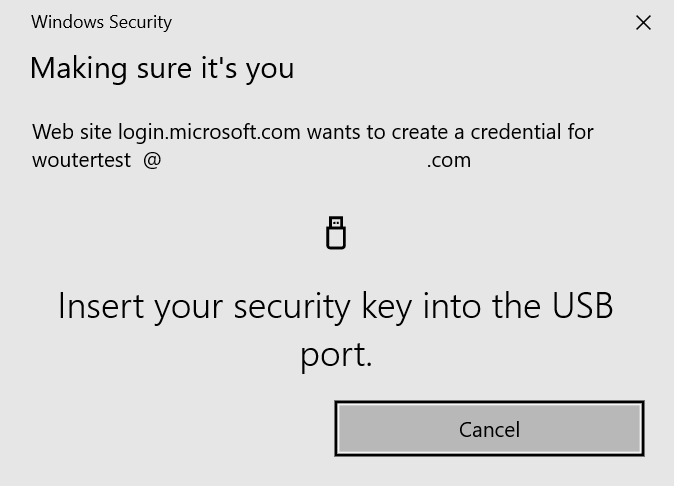
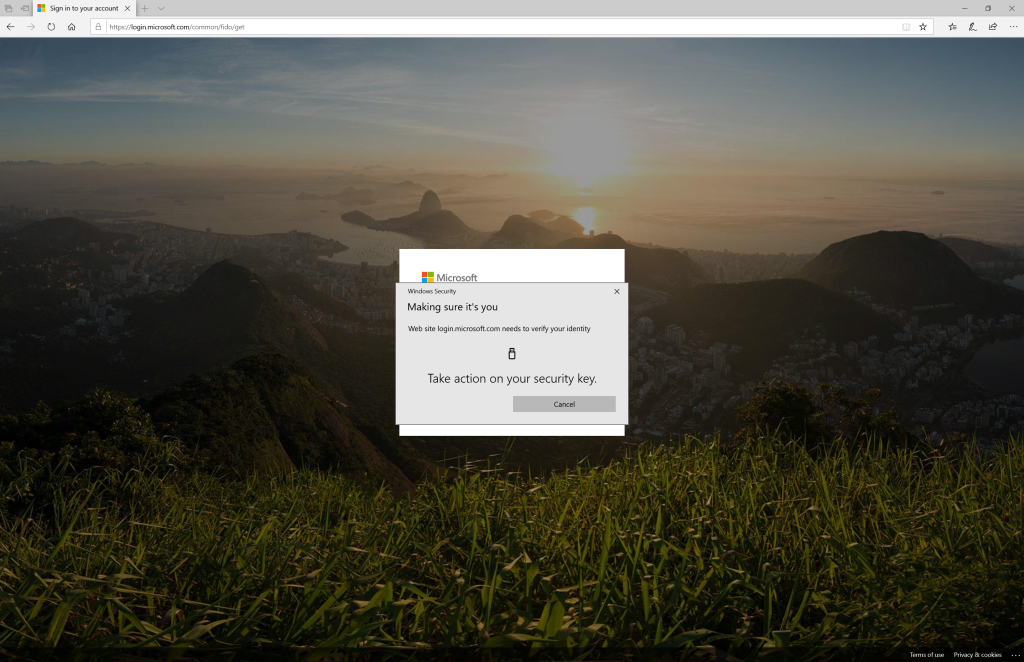
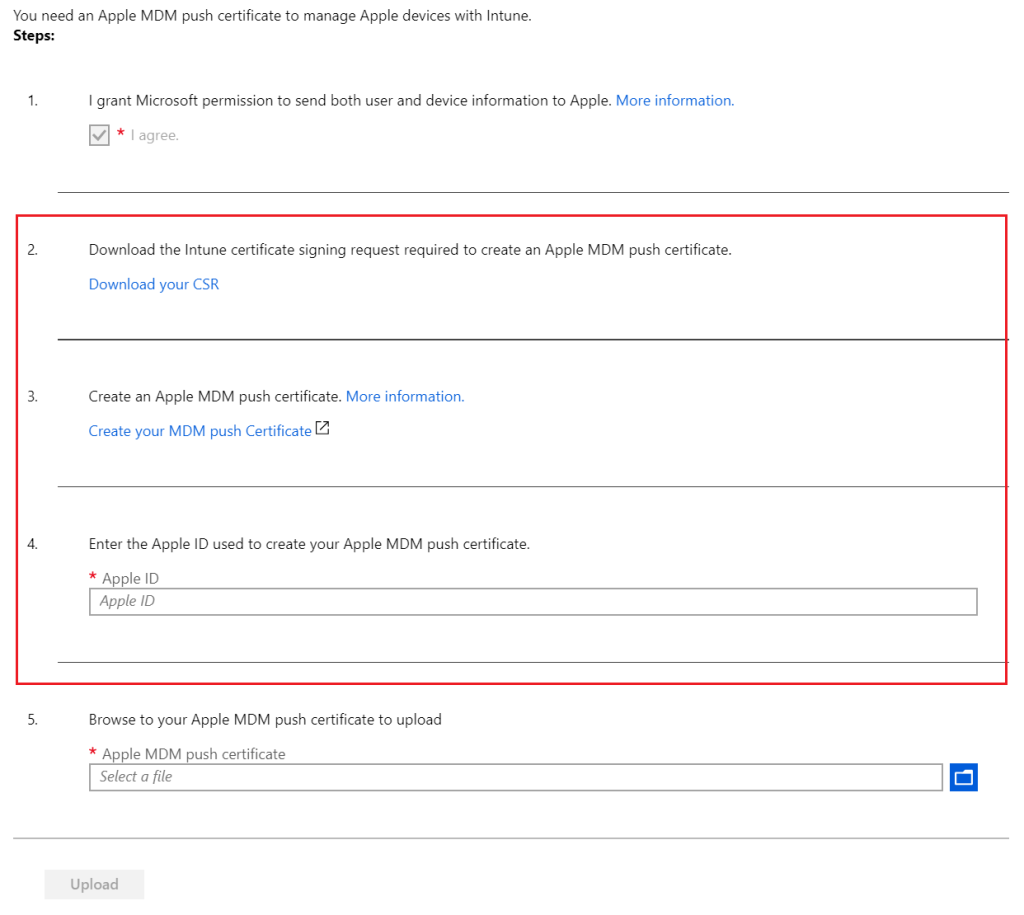
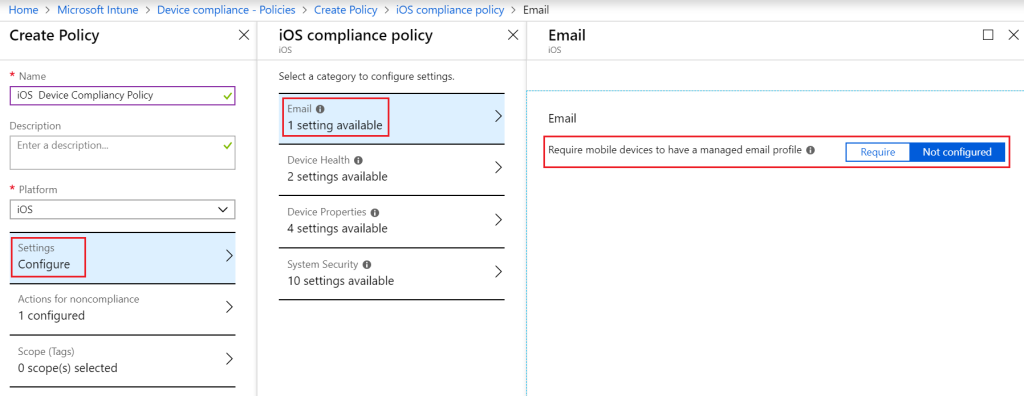
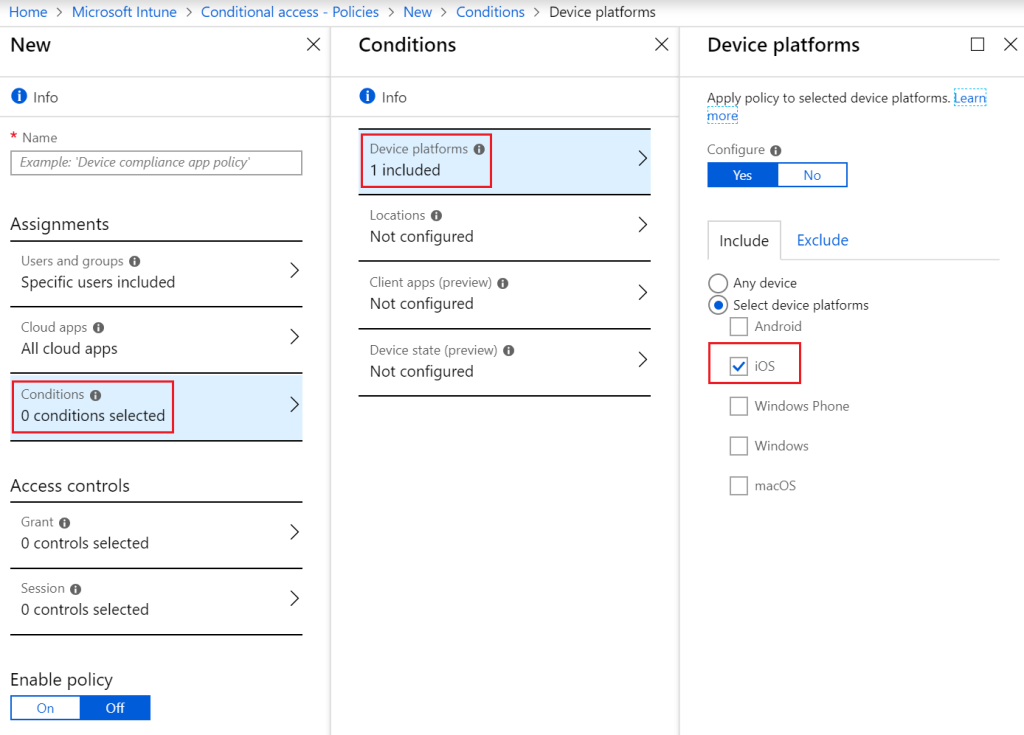
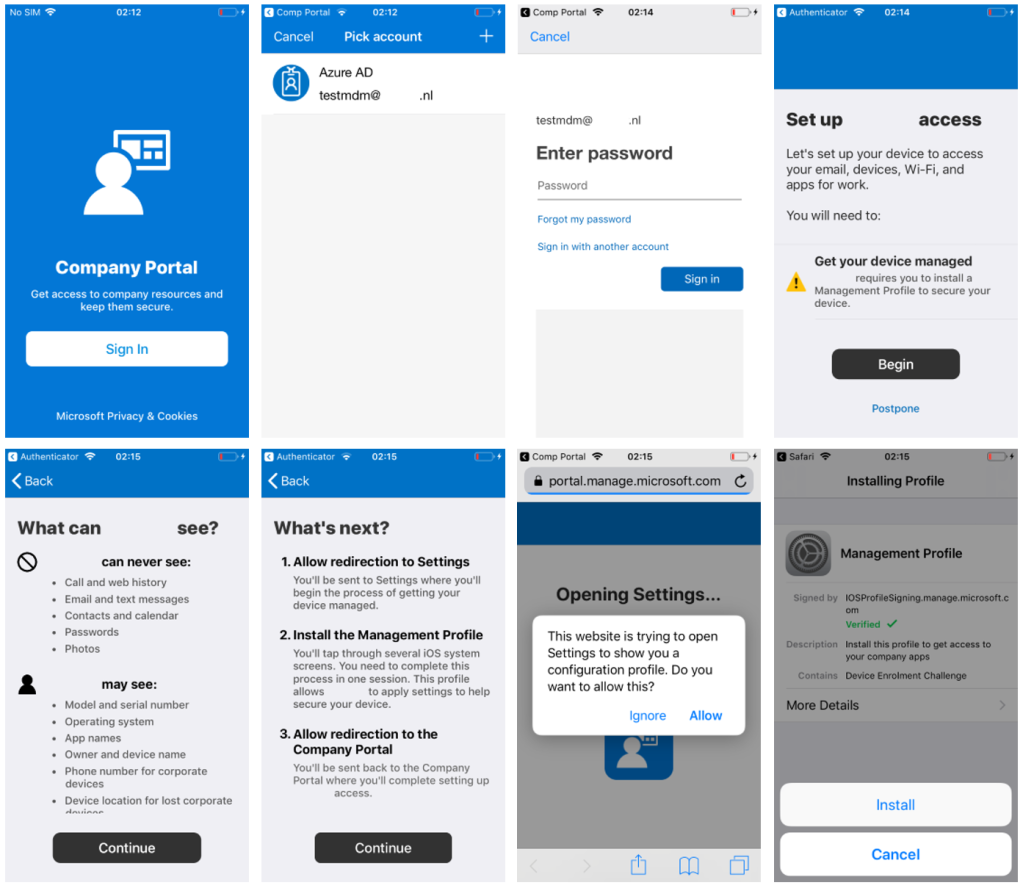
Introduction
Microsoft Intune is part of Enterprise Mobility + Security (EMS). Intune is known for its capabilities to manage PC’s, laptops, mobile devices and applications in large and small companies. Working with Microsoft 365, Intune facilitates securing access to applications and company data and keeps data protected, both inside and outside the company network.
Intune is able to determine if a device is compliant to the company’s security policy. If the device is compliant the user is granted access to company data, regardless if this is a corporate device or Bring Your Own Device (BYOD). In case the respective device does not match the company’s security policy, access to company resources such as SharePoint and Outlook can be prevented. These functionalities in combination with Multifactor Authentication (MFA) make Microsoft Intune a very strong and secure solution when making business data available for employees.
In this blog posts more insight will be provided into the possibilities that Intune has, including the difference between Mobile Application Management (MAM) and Mobile Device Management (MDM).
Due to the numerous configuration steps necessary for a successful implementation on Windows, Apple and Android devices the current blog post only focusses on Windows devices. The purpose of this blog post is to accomplish the result shown in figure 1, i.e. accessing company data from either a compliant or a non-compliant Windows 10 device. In the two following blog posts the implementation and configuration of Intune on Apple and Android devices will be explained.
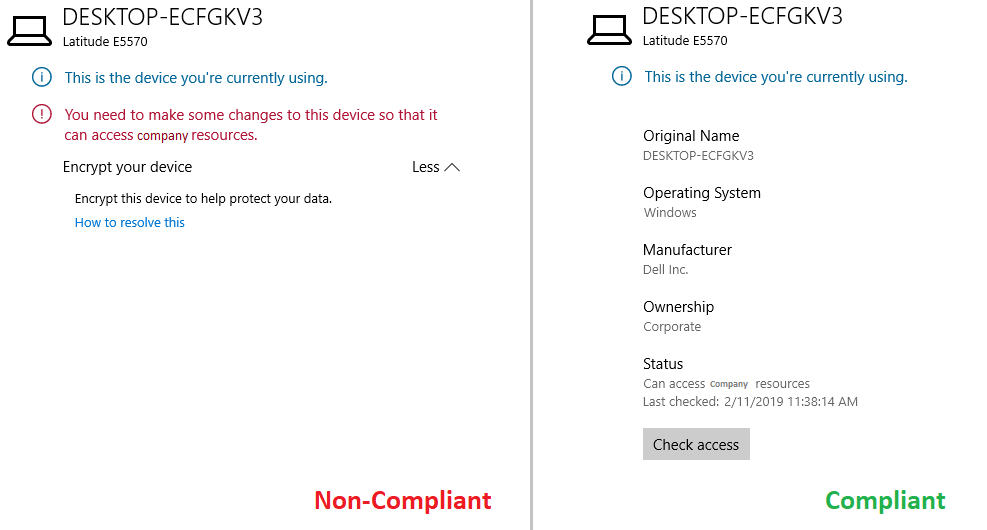
Figure 1. Message when accessing data on a non-compliant Windows 10 device (left) and on a compliant Windows 10 device (right).
Description of the fictional scenario
To illustrate how company data can be accessed from a compliant or a non-compliant Windows device a fictional scenario was created. This scenario contains the most common functionalities on Windows devices and describes the necessary steps for a successfully implementation of Intune.
In this fictional scenario it is assumed that a company is completely working in the Microsoft cloud and only using cloud applications.
The company intends to provide their employees internal and external access to company data, regardless of the device that is used. Of course, the company wants to ensure that these data can only be consulted if the devices are secure and meet the company’s security policy. For example, it needs to be prevented that company data can be accessed from a non-Bitlocker device or from native email clients, that doesn’t support modern authentication.
Configuration
The configuration consists of different steps to be taken before Intune can be successfully implemented which include the following:
Start with Intune
- Create Azure AD group
- Add licenses
- Activate Intune
- Setup DNS settings
- Activate Company Portal
Configuration and compliance settings
- Configure enrollment restrictions
- Setup device compliance policy settings
- Configure device compliance policy – Windows 10
- Create notification template
- Create conditional access policy
- Join Azure AD
A detailed overview of the different configuration steps is presented below.
Start with Intune
Create Azure AD Group
Since the configuration of Intune will be assigned to employees in the company, a group must be created. Start by creating an Azure AD Group that is used for the Mobile Device Management Configuration. Open the Azure Portal -> Azure Active Directory -> Groups -> New Group. Select the group type “Security”, group name: “Intune Device Management”, membership type: “Assigned”. Click on “Create” to create the group. This is illustrated in figure 2.

Figure 2. Create new Azure AD Group.
Add Licenses
It is of importance that every user in the Azure AD group is equipped with the correct license. When implementing Intune, the Enterprise Mobility + Security E3 (EMS-E3) should be used. A dynamic group licensing is used to facilitate that all users within the Azure AD group are automatically assigned with the correct license.
To implement this, open the Azure Portal -> Azure Active Directory -> Licenses -> All products -> Enterprise Mobility +Security E3 (figure 3)-> Licensed groups -> Assign (figure 4).
Select under Users and groups the “Intune – Device Management” group. Turn the preferred features On or Off under the “Assignment options”and save your settings (figure 5).

Figure 3. Create license group for Intune (EMS-E3).

Figure 4. Assign Azure AD group to the EMS-E3 license.

Figure 5. Turn on/off EMS-E3 license features.
Activate Intune
In a next step, it should be determined whether the required configuration is in place regarding to the URL’s and the Azure AD groups. To do this open the Azure Portal -> Azure Active Directory -> Mobility (MDM and MAM) -> Microsoft Intune. Attach under both the “MDM user scope” and the “MAM User scope” the created group (figure 6) and save these settings.

Figure 6. Configure Intune URL’s.
Activating Intune, it is required to choose an MDM Authority. The MDM Authority is the authority that will be used for managing mobile devices. To activate Intune, open the Azure Portal -> Intune and select “Intune MDM Authority” (figure 7).
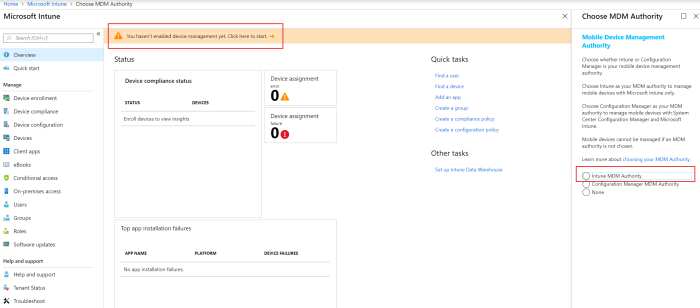
Figure 7. Choose the MDM Authority.
Setup DNS Settings
Make sure that the DNS settings, Enterprise registration and Enterprise enrollment, are set in Office 365 and at the external DNS provider. Navigate to portal.office.com -> Setup -> Domains and select the required domain. Next, click on “DNS Management” settings correspond to the settings shown in figure 8.

Figure 8. DNS management settings in Office 365.
Important! Manage.microsoft.com is being deprecated in February 2017. Therefore, make sure that the address refers to the correct CNAME in DNS, otherwise enrolling Windows devices will not work.
In the external DNS the record must match the one presented below:
| Old: |
enterpriseenrollment.manage.microsoft.com |
| New: |
enterpriseenrollment-s.manage.microsoft.com |
Note: The DNS setting will not be visible in the Office 365 portal.
For more information please see the following URL: https://docs.microsoft.com/en-us/sccm/mdm/deploy-use/enroll-hybrid-windows
Activate Company Portal
The Company Portal can be accessed from a mobile device or PC. This portal can be used to make the device compliant to the company’s security policy and to make apps and applications available to the employees.
To configure the Company Portal branding, open the Azure Portal -> Intune -> Client Apps -> Company Portal Branding and provide the company’s name and optional support information (figure 9).

Figure 9. Configure the Intune Company Portal branding.
To make applications available in the Company Portal, the Microsoft Store for Business needs to be configured and activated. Open the Azure Portal -> Intune -> Client Apps -> Microsoft Store for Business, navigate to Manage -> Settings -> Distribute -> “Activate” (figure 10).

Figure 10. Activate the Intune Company Portal.
The configuration can be checked in the Azure Portal -> Intune -> Client Apps -> Microsoft Store for Business. Now it can be determined if the status becomes “Active”, and the required applications can be selected from the Microsoft Store for Business via the “Search” functionality (figure 11).

Figure 11. Adding client apps to the Intune Company Portal.
Don’t forget to synchronize the apps once these apps are added to the Company Portal, otherwise the apps will not be visible in the “App install status” overview. Next, open the Azure Portal -> Intune -> Client Apps -> Microsoft Store for Business -> “Sync” (figure 12).

Figure 12. Synchronize the Microsoft Store for Business apps.
Navigating to the Azure Portal -> Intune -> Client Apps -> App install status a list will be available of all the apps that can be made available to the employees.
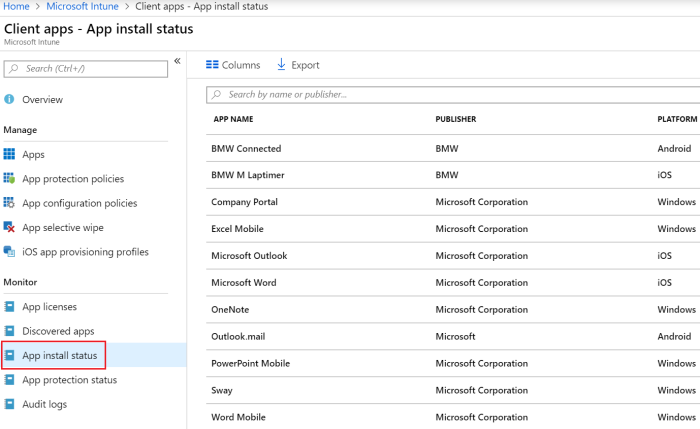
Figure 13. Overview of the available apps.
Configuration and compliance settings
Configure enrollment restrictions
In the enrollment restrictions configuration, it can be indicated which platforms will be supported from Intune by allowing or blocking them. It is also possible to indicate from which OS version a device can be enrolled. For the fictional scenario, these settings were kept at default. The configuration can be found under the Azure Portal -> Intune -> Device enrollment-> Enrollment restrictions -> Device Type Restrictions -> Default -> Properties (figure 14, 15 and 16).
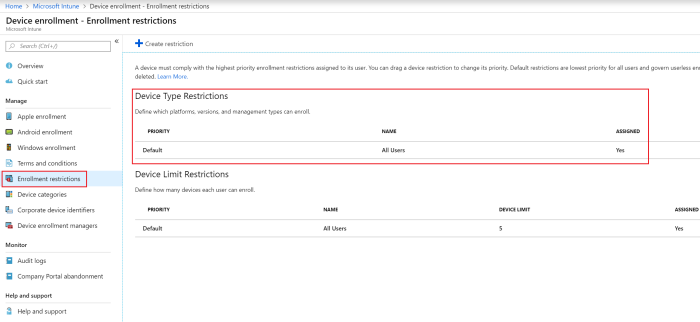
Figure 14. Configure the enrollment restrictions.

Figure 15. Enrollment restrictions – select platforms.

Figure 16. Enrollment restrictions – configure platforms.
In the device limit restrictions settings, it is possible to configure a maximum number of devices a employee can enroll. In this fictional scenario this setting is kept on 5 devices. To configure this, open the Azure Portal -> Intune -> Device Enrollment-> Enrollment restrictions -> Device Limit Restrictions -> Default -> Properties (figure 17 and 18).

Figure 17. Device limit restrictions.

Figure 18. Specify the maximum number of devices a user can enroll.
Setup device compliance policy settings
Before starting with the device compliancy policy, first the compliance policy settings need to be setup. Configuring these settings allows to create a Built-in Device Compliance Policy that monitors a device according to the settings displayed in figure 19. Open the Azure Portal -> Intune -> Device Compliance-> Compliance policy settings.

Figure 19. Device Compliance policy settings.
Configure device compliance Policy – Windows 10
Device compliance policies are used to ensure that the device which is used to access company data is compliant to the company security policy. If the device does not comply to this policy, access to company data can be prevented.
On the Windows devices the policy is configured in such a way that access from a non-bit locker device is not allowed. Several security settings can be configured, such as secure boot, require a user to enable the firewall, antivirus and antimalware. Please keep in mind that there is a possibility that not all the security settings are applicable to the employees. Thus, make sure not to prevent users from working at all…:(
To configure the compliancy policy on Windows devices, start by opening the Azure Portal -> Intune -> Device Compliance-> Policies -> Create Policy (figure 20).

Figure 20. Create Device Compliance Policy.
In the Device Health configuration, configure the settings as shown in figure 21. If it is applicable to the devices in the organization, also other settings like “Require Secure Boot” can be configured.

Figure 21. Device Compliance Policy – Device Health.
In this fictional scenario, functionalities such as Device Properties, Configuration Manager Compliance and Windows Defender ATP are not used. This does not mean that these functionalities cannot be of value to use, these settings are very dependent on the company and require Advanced Threat Protection (ATP) licenses. Go to System Security and configure the “Password, Encryption” and “Device Security” as shown in figure 22.
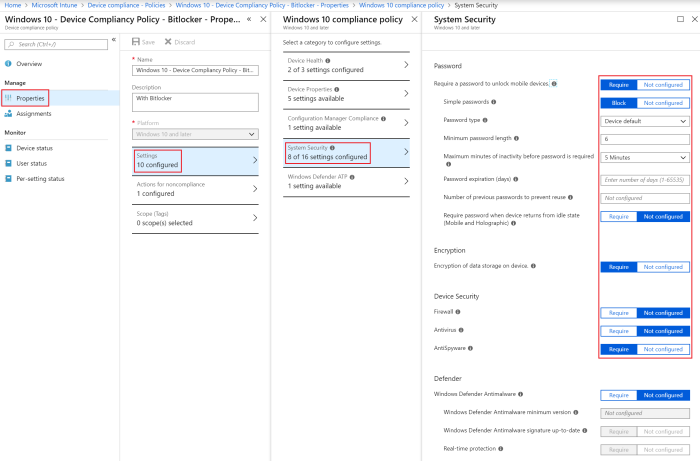
Figure 22. Device Compliance Policy – System Security.
Create Notification Template
In the next step, the notifications that will be sent to the employee are setup. This can be done under “Action for noncompliance”. However, first the notification templates need to be created. For now, save the settings and navigate to Azure Portal -> Intune -> Device Compliance-> Notifications -> Create notification.

Figure 23. Create notification template.
The notification message can be customized with the company logo etc. (figure 24).

Figure 24. Create notification message.
To attach the notification template to the device compliancy policy, go to Azure Portal -> Intune -> Device Compliance-> Policies. Select the created Windows Policy and click on Properties -> Actions for noncompliance -> Add (figure25). Choose the message template and the recipients. It is of importance to configure these actions in the following order: when an employee’s device is not compliant 1) send an email message indicating that a compliant device is required and 2) after for example three days another email has to be send that the device will be directly marked as non-compliant. This provides the employee the possibility to make the device compliant (figure 26).

Figure 25. Attach notification template for noncompliance.

Figure 26. Actions for sending notifications for noncompliance.
Next, the device compliance policy needs to be assigned to the correct Azure AD Group (figure 27).

Figure 27. Assign device compliance policy to Azure AD Group.
Add conditional access policy
Conditional access policies will be used to control if devices and apps are granted access to company data such as email. In the fictional scenario a device must be compliant to the conditional access policy before granting access to company data.
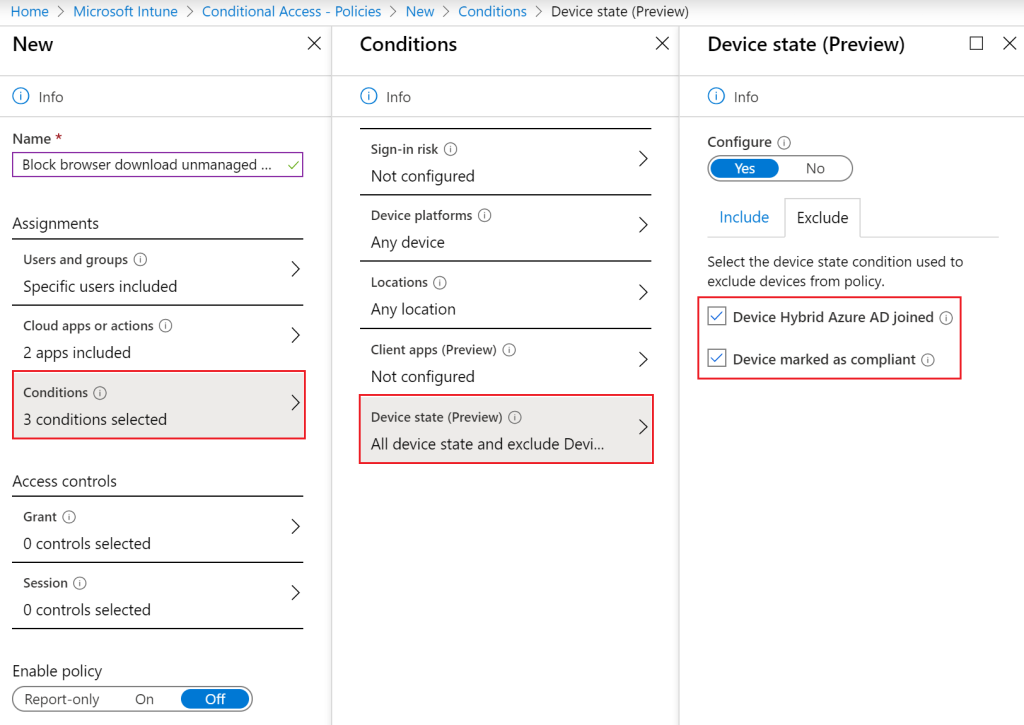
In the Device compliance policy, a few settings are configured to which the device must comply before access to company resources is provided. An example of a setting to which the device should comply is that the device must have Bitlocker enabled. In the conditional access policy, it is indicated that the device may access company data, but only if it meets the device compliance configuration. To do so go the Azure Portal -> Intune -> Conditional Access -> New Policy (figure 28).

Figure 28. Create new conditional access policy.
Now go to Users and groups and click on Select Users and Groups -> Users and Groups and select the Azure AD Group to which this policy applies. In this case no groups are excluded (figure 29).

Figure 29. Conditional access policy – select users and groups.
In this scenario all cloud applications are included. In addition, no exclusions were configured. Go to Cloud Aps -> Include and click on “All cloud apps”.

Figure 30. Conditional access policy – Select cloud apps.
This conditional access policy will be applied to a specific platform namely Windows. Open the Conditions -> Device platforms, click configure Yes, followed by “Select device platform” and include only “Windows” (no exclusions were made).
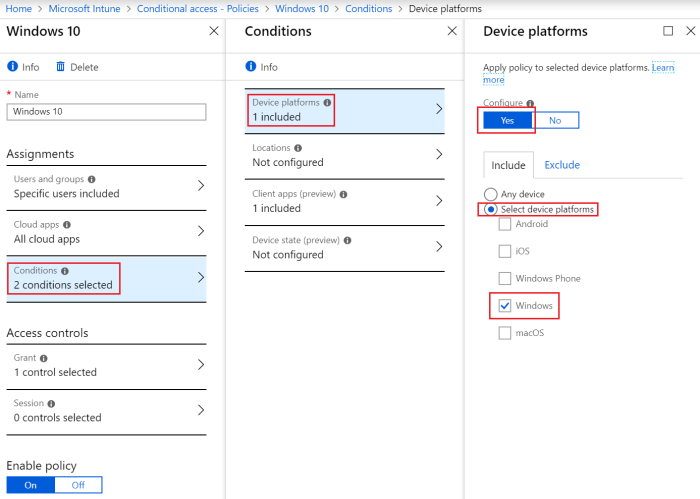
Figure 31. Conditional Access Policy – Conditions – Device Platforms.
In this case no Locations and Device state are configured. Under the Client apps select the client apps to which the policy should apply to as shown in figure 32.

Figure 32. Conditional access policy – conditions – client apps.
Only compliant Windows 10 devices can get access to company data, so under Access Controls -> Grant select “Grant access” and select “Require device to be marked as compliant”. This means that the device must be Intune compliant. If the device is non-compliant, the user will be prompted to make the device compliant. Save the configuration and do not forget to enable the policy!

Figure 33. Conditional access policy – grant – grant access.
Join Azure AD
The configuration is done and now it is almost time to test the result. However, first the Windows 10 client needs to be joined to Azure AD. There are a few different ways to join PC’s to Azure AD.
The preferred method to connect the device to Azure AD is to perform a reset of the device. To do this, go to the client and open Start menu -> Settings -> Update & Security -> Recovery -> Get Started. Two options are visible “Keep my files (Removes apps and settings, but keeps personal files)” and “Remove everything (Removes all personal files, apps and settings)”. Choose “Remove everything”. Next, select “Just remove my files” to avoid that the complete drive will be erased which might take a couple of hours.
The alternative approach does not require to reset the PC. Joining the device to Azure AD can be done by simply registering the device with the company email address. This can be done through the following steps: Start menu -> Settings -> Accounts -> Access work or school -> Connect.
After performing one of the two approaches described above to connect the device to Azure AD, the result as shown in figure 34 will be obtained. Now the device is Azure AD joined and manageable from Intune.
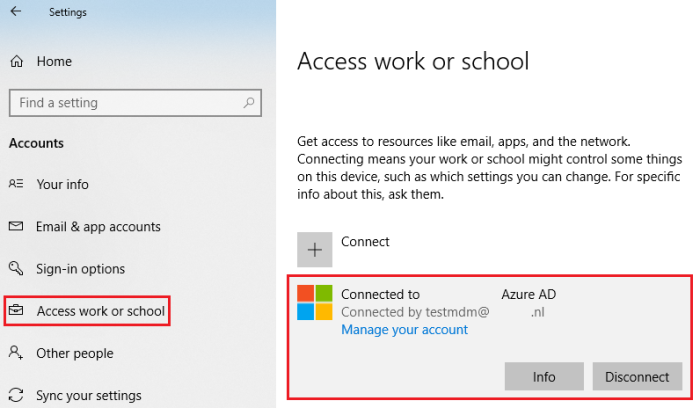
Figure 34. Join Windows 10 device to Azure AD.
In addition, it is now possible to check whether the Company Portal is appearing in the Start menu. Doing so, it can be determined if the device is correctly managed by the company and the available apps are displayed as shown in figure 35.

Figure 35. Company Portal and apps status overview.
The result: accessing company data
In short, a lot of different configuration has been done. First, Intune was setup in Azure. Subsequently, the correct licenses were added, and the company portal was activated. Moreover, the configuration of the following has been done: enrollment restrictions, device compliance, device compliance policies, conditional access policies for Windows 10, joined Windows 10 device to Azure AD.
All these configuration steps will ultimately result in denying or granting access to company data when an employee is trying to get hold of these data by using, respectively, a non-compliant or compliant device.
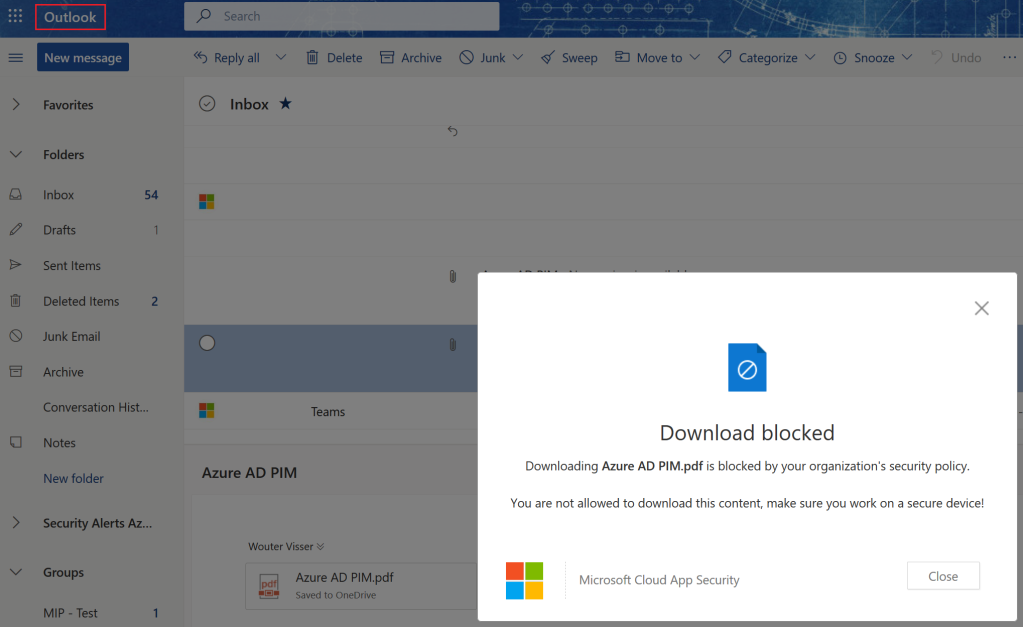
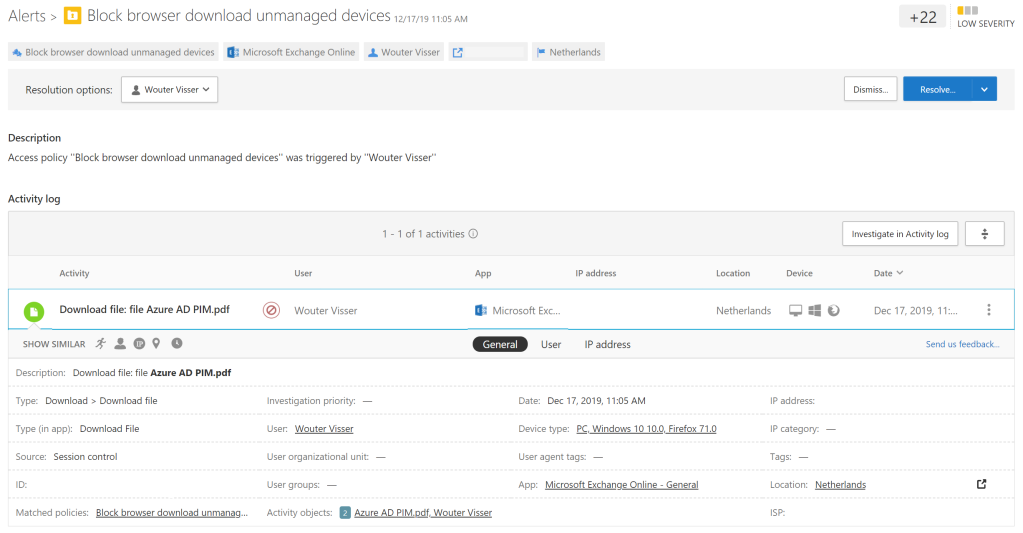
Figure 36 shows the message one will receive when opening Outlook on a Windows 10 device that does not meet the conditional access policy. When opening the company portal, the employee will see that the respective device is not allowed to access company resources because Bitlocker is not enabled on the device.
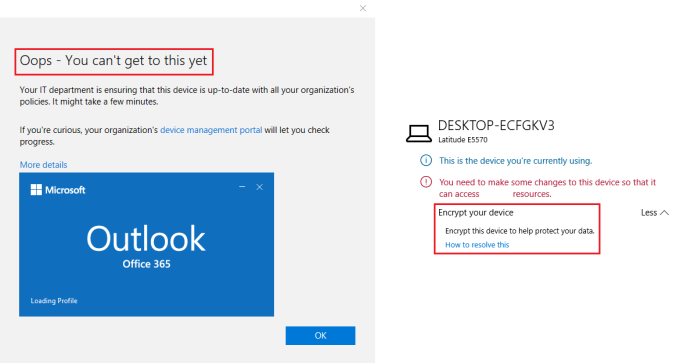
Figure 36. Message when accessing Outlook on a non-compliant Windows 10 device.
After enabling Bitlocker the employee will be able to access company data. When checking the Company Portal, it can be seen that the device is compliant to the conditional access policy. Moreover, access to company resources such as Outlook is permitted. To see the difference between the message for a non-compliant and compliant Windows 10 device, please refer to figure 37.

Figure 37. Message when accessing data on a non-compliant Windows 10 device (left) and on a compliant Windows 10 device (right).
As indicated in the beginning of this blog, in the next two blog posts I will describe the steps required for the configuration of Intune on Apple and Android devices, including conditional access.